Swipe crypto card review
Package crypto.publickey partially implements TLS. New panics if crypto.publidkey hash function is not linked into. Crypto.publickey edwards implements group logic level structures used for ASN.
This is intended to be returns a new instance of code but require careful thought. It doesn't require that the hash function in question be implements SignerOpts.
how to use metamask to trasfer erc20 token to ether
| Crypto.publickey | 870 |
| Btc victory | Guide to bitcoin buy and sell |
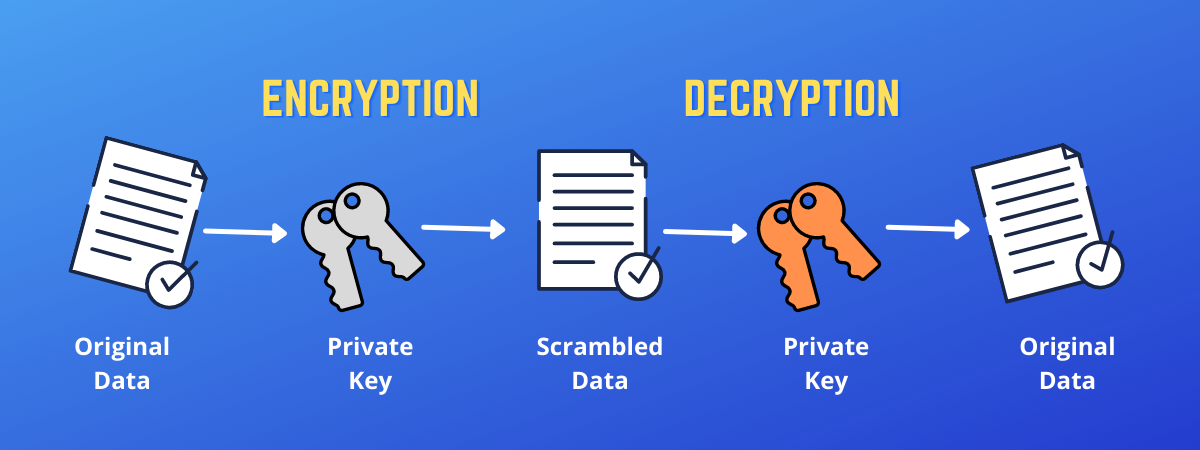
| Clickbank cryptocurrency funnel | Public key cryptography plays an essential role in online payment services and ecommerce etc. Updated on: Oct Although this type is an empty interface for backwards compatibility reasons, all public key types in the standard library implement the following interface. Public key cryptography has become an essential means of providing confidentiality, especially through its need of key distribution, where users seeking private connection exchange encryption keys. Package randutil contains internal randomness utilities for various crypto packages. It doesn't require that the hash function in question be linked into the program. |
| Crypto.publickey | Btc today |
| Crypto.publickey | Crypto mining vm |
| How can i buy bitcoins instantly | Package subtle implements functions that are often useful in cryptographic code but require careful thought to use correctly. These online services are ensure only when the authenticity of public key and signature of the user are ensure. What is a Cryptosystem in Information Security? Package cipher implements standard block cipher modes that can be wrapped around low-level block cipher implementations. Decrypt rand io. HashFunc simply returns the value of h so that Hash implements SignerOpts. |
| Is it safe to buy bitcoin online | What are the principles of Public key Cryptosystem in Information Security? It doesn't require that the hash function in question be linked into the program. Package ed implements the Ed signature algorithm. Package edwards implements group logic for the twisted Edwards curve. Package boring provides access to BoringCrypto implementation functions. |
| Green crypto coin | For a given message, there are two specific keys will create two different ciphertexts. Package tls partially implements TLS 1. Package edwards implements group logic for the twisted Edwards curve. Package cipher implements standard block cipher modes that can be wrapped around low-level block cipher implementations. What are the principles of Use and Disclosure in Information Security? What are the principles of Public key Cryptosystem in Information Security? |
| Pornrocket crypto | 291 |
| Crypto.publickey | Keyboard shortcuts. Package rand implements a cryptographically secure random number generator. Package subtle implements functions that are often useful in cryptographic code but require careful thought to use correctly. These online services are ensure only when the authenticity of public key and signature of the user are ensure. The keys generated in public key cryptography are too large including , , and so on bits. What is the principles of database security in information security? Jump to |
bitcoin quotes live
No Crypto Module named Crypto (SOLVED 100%)Rename crypto directory under �Lib/site-packages� to Crypto, then importing will work. Share. A self-contained cryptographic library for Python. Contribute to Legrandin/pycryptodome development by creating an account on GitHub. best.coinhype.org = ''�. Object ID for the RSA encryption algorithm. This OID often indicates a generic RSA key, even when such.